What is encryption?
-
Due to the Data (Use and Access) Act coming into law on 19 June 2025, this guidance is under review and may be subject to change. The Plans for new and updated guidance page will tell you about which guidance will be updated and when this will happen.
What is encryption and how can it protect personal information?
Encryption is a process that uses a secret key to encode information, ensuring that only those with access to the key can read it. Decryption is the opposite - the secret key decodes the information and makes it useful again.
Some algorithms use different keys for encryption and decryption. Without the correct key, the information remains inaccessible, protecting it from unauthorised or unlawful access.
It is theoretically possible to decrypt the information without the key by attempting every possible combination. This is called a brute force attack. But this can take an impractically long time - potentially millions of years - depending on the computing power and key type.
This means encryption provides a suitable safeguard against unauthorised or unlawful processing of personal information, especially when alternative measures are not feasible.
Today, most information transmitted over the internet is encrypted. Most smartphones and similar devices are protected (eg by the phone’s passcode). These common forms of encryption safeguard people without them needing to think about it.
What types of encryption are there?
There are two types of encryption in widespread use today: symmetric and asymmetric. The difference is whether or not the same key is used for encryption and decryption.
What is symmetric encryption?
Symmetric encryption is where the same key is used for both processes. This means it is critical to use a secure method to transfer the key between sender and recipient.
Symmetric encryption is useful in scenarios when:
• there is a secure or separate way to share a key, or both; or
• the key does not need to be shared (eg if you encrypt and decrypt data on your local device).
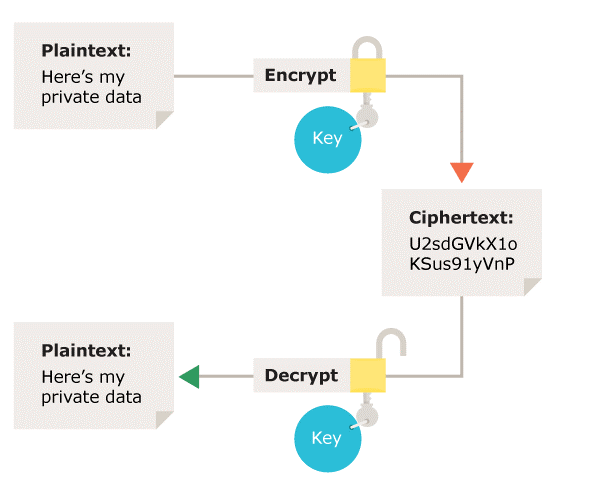
Figure 1: Symmetric encryption – Using the same key for encryption and decryption
What is asymmetric encryption?
Asymmetric encryption is where one key is used for encryption and a different key is used for decryption. One of the keys is typically known as the private key and the other is known as the public key.
The private key is kept secret by the owner and the public key is either shared among authorised recipients or made publicly available.
This typically means that any party can encrypt data, but only the owner of the private key can decrypt it.
This can avoid or greatly reduce the complexity of securely distributing keys when compared to symmetric encryption. Data can therefore be sent with reduced risk of unauthorised or unlawful access to it.
Asymmetric encryption is useful in scenarios where both parties have the infrastructure in place to facilitate its use.
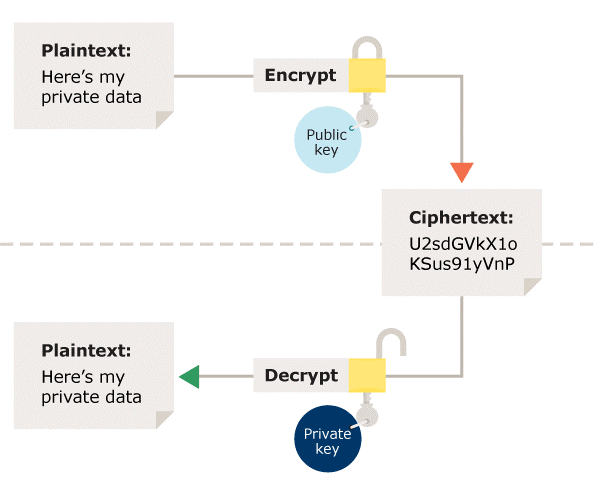
Figure 2: Asymmetric encryption – Using a different key for encryption and decryption
How can we use encryption?
There are a few ways you can use encryption, depending on your purposes.
Encryption and data storage
This encrypts data stored on a device or network in such a way that it is unintelligible to unauthorised users without a key. It ensures that the data is kept secure against risks of theft or unauthorised access. You can use this type of encryption when you store data on devices (eg servers, PCs, laptops, mobile phones, removable storage) and in backups.
Encryption and data transfer
This protects data as it moves across a network, such as the internet. The data is shielded from interception or eavesdropping. Even if the communication is intercepted, the data remains unintelligible without the decryption key. You can use this type of encryption when you send and receive data online (eg through websites or over email).
Encryption when processing
This protects data when it is being used. Normally, to make use of data protected by encryption, it must first be decrypted and turned back into plaintext. In recent years, technological advances mean that it is possible to perform computations on encrypted data without decrypting it first. This maintains the data’s security while still enabling it to be used.
An example of this type of encryption is ‘homomorphic encryption’. We discuss this in more detail in our guidance on privacy-enhancing technologies (PETs).
Further reading – ICO guidance