You must carry forward your privacy planning from previous stages all the way into the finished product or feature. Careful privacy engineering makes systems more reliable and protects people.
Define the minimum personal information you require
You must only collect the personal information you really need. The more information you handle, the greater the data management overheads and potential privacy risks.
You should:
- review any data maps you created during kick-off, and check you are using the minimum personal information you need to make the product or feature work;
- clarify what the feature or product is trying to achieve and double-check whether you really need personal information to achieve your outcomes;
- question any personal information collection that seems unnecessary and raise it with your data protection officer or legal colleagues. If the processing isn’t necessary, it may be unlawful; and
- check that people can access as much functionality as possible without having to provide personal information.
Further reading
Enhance privacy and security with technical measures
Proper security engineering protects people from privacy harms. You should:
- store private, sensitive, or secret information like usernames, passwords, and cryptographic keys securely. You should not store passwords in plaintext;
- use hashing, encryption, or other privacy-enhancing methods to protect information in storage, backups, and in transit;
- consider how you could use novel architectures for information handling, such as federated, decentralised, or on-device processing to enhance privacy and security.
Example
The makers of a mobile OS offer voice recognition functionality. Previously, this has involved processed speech audio being sent to centralised cloud systems for processing. Now, speech snippets are processed directly on a user’s handset and converted into text strings that are interpreted by the OS itself.
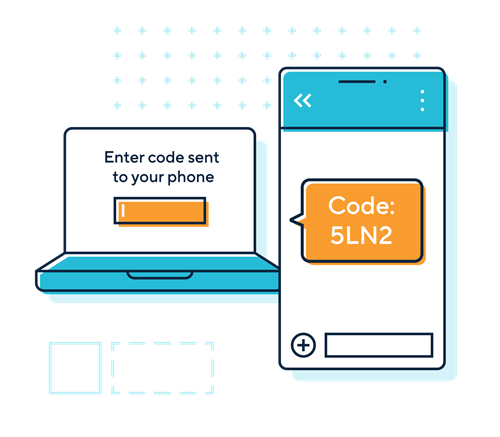
- offer people enhanced security options such as two-factor authentication, where appropriate, to help people stay secure. If your product uses default passwords, you should design ways for people to replace these with secure passwords of their choice.
Ensure people can exercise their data rights
People have a range of individual rights under UK GDPR. Any organisation processing personal information must ensure these rights can be exercised:
- As discussed in the design phase, you could consider letting people exercise these rights directly through your product.
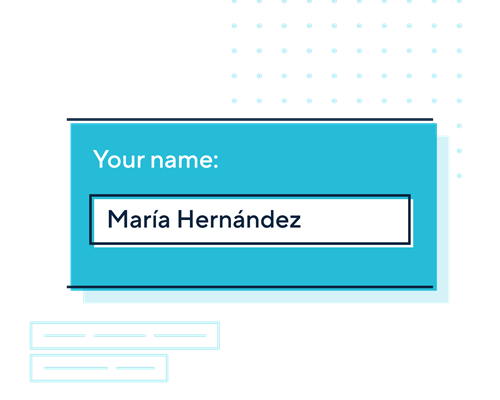
- You must ensure people can enter their personal information accurately and request amendments through the right to rectification.
Example
A developer building a health-tech product takes extra care to ensure name input fields accept accented characters and non-Western name formats. They also review database fields that store people’s heights and weights, and removes unreasonable limits on what values the system considers valid, so people outside these ranges can have their personal information recorded accurately.
Protect personal information during development
Your organisation must process personal information securely by ‘appropriate technical and organisational measures’. To do this, you should:
- set up proper access control systems so other people (including internal users) can only access the information they need to see;
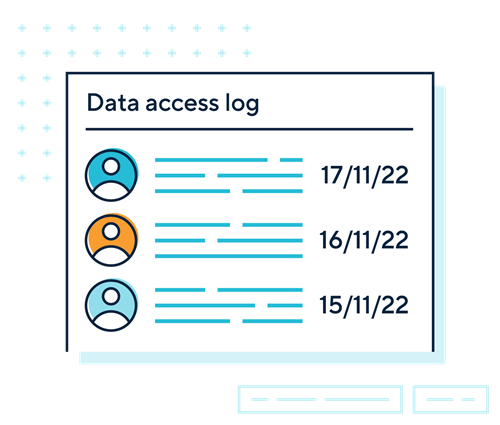
- consider logging data interactions, such as who has accessed or modified data;
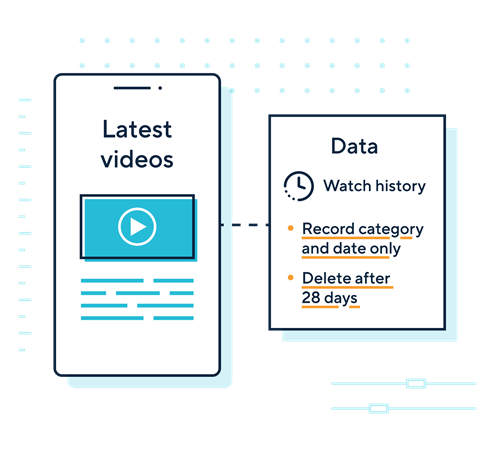
- establish retention policies so you aren’t holding onto information beyond its proper lifespan;
- check all third-party libraries you use are secure and not likely to leak private information;
- embrace QA or code review processes so teammates can verify your code is secure and free of vulnerabilities; and
- understand where adversaries might try to attack your system, and take steps to reinforce any vulnerable areas.
You could also choose to follow established secure coding practices, such as the National Cyber Security Centre’s Secure development and deployment guidance and OWASP’s Secure Coding Practices Quick Reference Guide.