- What is a zero-knowledge proof and what does it do?
- How do ZKPs assist with data protection compliance?
- How does using ZKPs impact our ability to achieve the purpose of the processing?
- What are the risks associated with using ZKPs?
What is a zero-knowledge proof and what does it do?
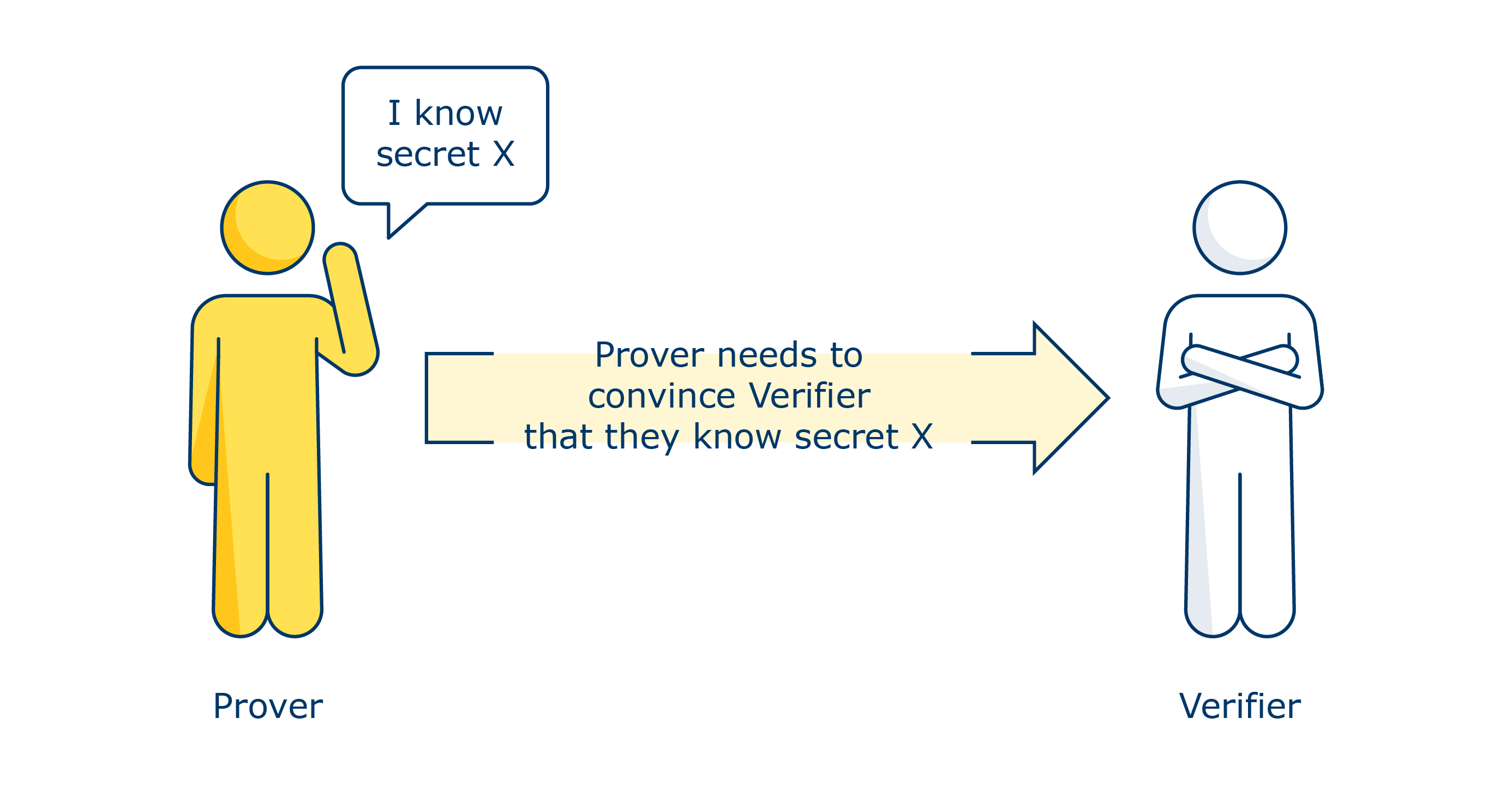
A zero-knowledge proof (ZKP) refers to any protocol where a prover (usually a person) is able to prove to another party (verifier) that they are in the possession of a secret (information they know but is unknown to the verifier).
For example, a prover can prove their age without revealing what it actually is. The prover can use a ZKP to prove to the verifier that they know a value X (eg proof they are over 18), without conveying any information to the verifier, apart from the fact that the statement is true.
Existing applications of ZKPs include:
- confirmation a person is of a certain age (eg legally able to drive), without revealing their birth date;
- proving someone is financially solvent, without revealing any further information regarding their financial status; or
- demonstrating ownership of an asset, without revealing or linking to past transactions; and
- supporting biometric authentication methods, such as facial recognition, fingerprint sensor and voice authorisation on mobile devices.
ZKPs can be interactive, (ie require the service or verifier to interact with the prover), or non-interactive.
How do ZKPs assist with data protection compliance?
If you use a ZKP service, the information you receive (eg proof that someone is over a particular age), is likely to still relate to a person depending on the nature of the query. Therefore, it is still personal information. You could use ZKPs to help you achieve data protection compliance with:
- the data minimisation principle as they limit the amount of personal information to what is required; and
- the security principle as confidential information, such as actual age, does not have to be shared with other parties.
How does using ZKPs impact our ability to achieve the purpose of the processing?
The algorithms and functions underpinning ZKPs provide a probable certainty as to whether the information is correct or not. When applying a ZKP to the design of a processing operation, you should assess whether this uncertainty reaches sufficiently low value for the risk to be accepted in the framework of that specific processing.
What are the risks associated with using ZKPs?
Poor implementation of the protocol can cause weaknesses, for example:
- code bugs;
- compromise during deployment;
- attacks based on extra information that can be gathered from the way the ZKP protocol is implemented; and
- tampering attacks.
You must ensure that the technical and organisational measures you use are consistent with the underlying protocol specification, and you have taken appropriate measures to address any security risks.
Further reading
See the current ZKP community reference document (external link, PDF) for more information regarding advanced ZKP techniques, including their advantages, disadvantages and applications.